Russian Actors Weaponize Legitimate Services in Multi-Malware Attack
Ooda Loop
MAY 15, 2024
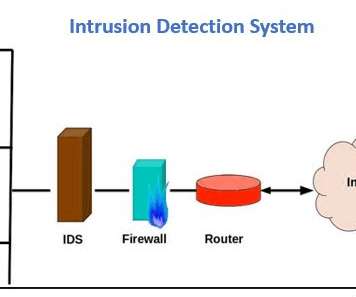
A novel cyber campaign by Russian speaking actors abused legitimate internet services, such as GitHub and FileZilla, to deploy multiple malware variants, Recorded Future has reported. This […]















































Let's personalize your content