How to Use Application Load Balancer and Amazon Cognito to Authenticate Users for Your Kubernetes Web Apps
DevOps.com
JULY 14, 2023
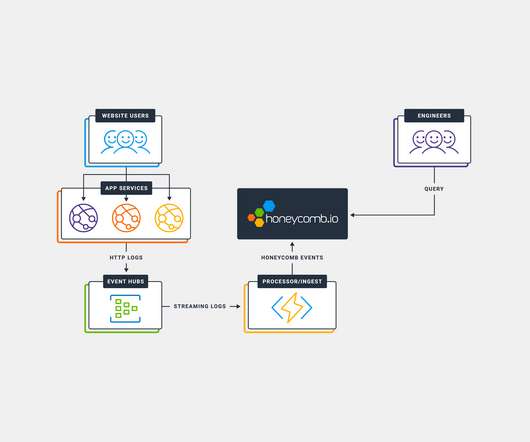
This post describes how to use Amazon Cognito to authenticate users for web apps running in an Amazon Elastic Kubernetes Services (Amazon EKS) cluster.



















































Let's personalize your content