How today’s enterprise architect juggles strategy, tech and innovation
CIO
APRIL 16, 2025
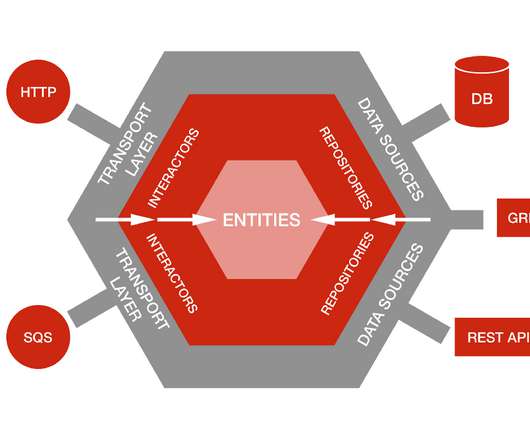
In a world where business, strategy and technology must be tightly interconnected, the enterprise architect must take on multiple personas to address a wide range of concerns. These include everything from technical design to ecosystem management and navigating emerging technology trends like AI.
















































Let's personalize your content