Six steps to creating a successful IT strategy: A guide for CIOs
CIO
OCTOBER 15, 2024
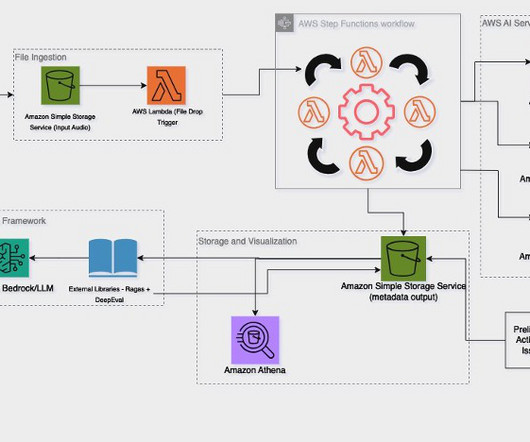
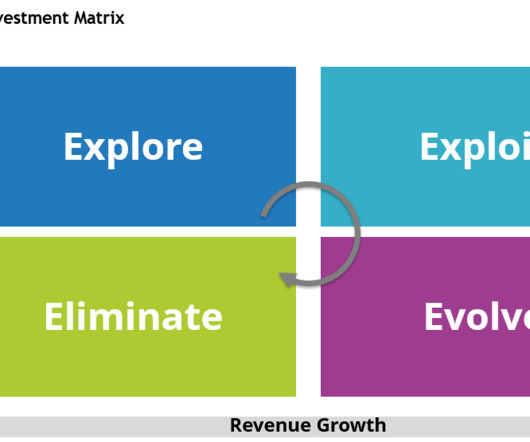
This requires evaluating competitors’ strategies; identifying strengths, weaknesses, and opportunities; and leveraging insights from the competitive market analysis team or similar teams within the organization. This process includes establishing core principles such as agility, scalability, security, and customer centricity.














































Let's personalize your content