Vibe Coding, Vibe Checking, and Vibe Blogging
O'Reilly Media - Ideas
APRIL 22, 2025
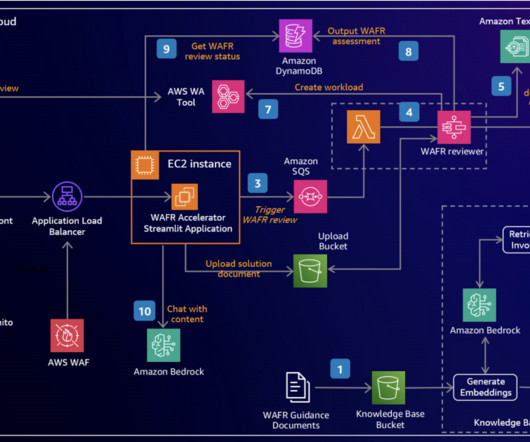
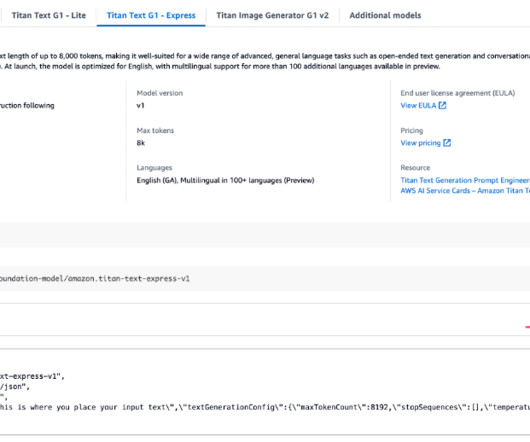
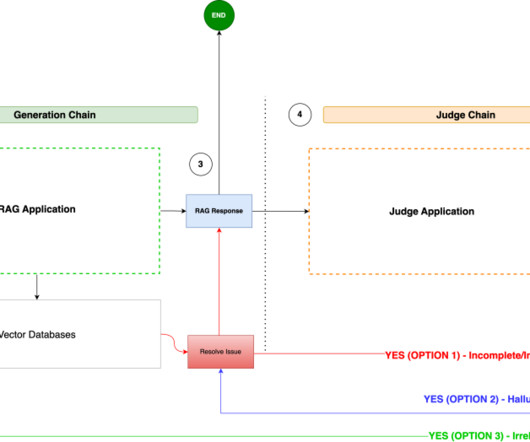
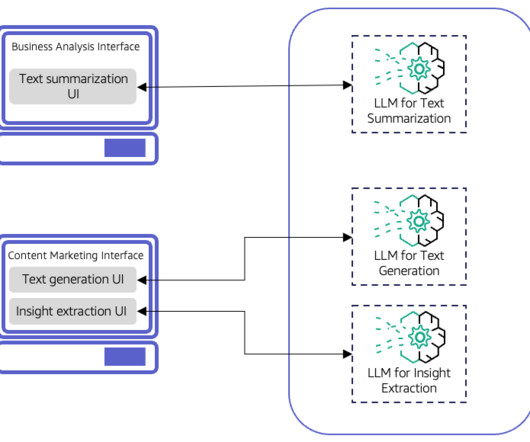
Some of you might have read my recent piece for O’Reilly Radar where I detailed my journey adding AI chat capabilities to Python Tutor , the free visualization tool that’s helped millions of programming students understand how code executes. Let me walk you through a recent example that perfectly illustrates this approach.














































Let's personalize your content