My New Year’s Resolution: Going Passwordless!
Ivanti
DECEMBER 29, 2021
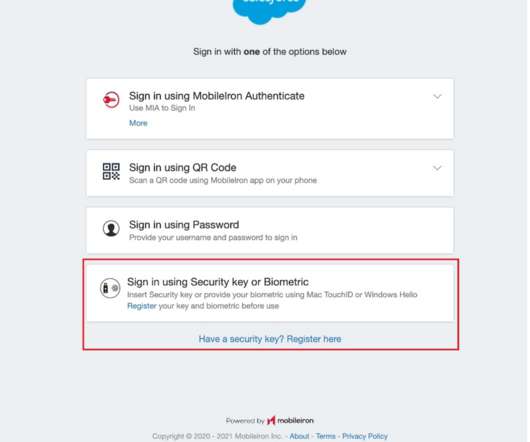
Also, with the resurgence of the Pegasus spyware that now exploits zero-day vulnerabilities in common apps like iMessage, FaceTime, Safari, WhatsApp, and others, stolen data – specifically credentials – allow attackers to gain a foothold onto a compromised device without the end user knowing. How can Ivanti help?



















Let's personalize your content