Operating System Characteristics (Features)
The Crazy Programmer
OCTOBER 23, 2021
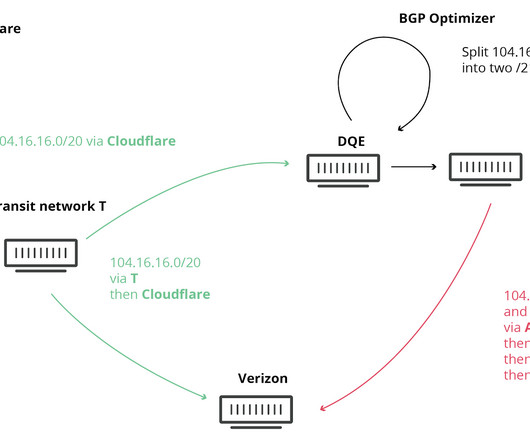
Do you know all the applications, including MS Office, editing software, browser, and games need a suitable environment to execute their task? The operating system is the software that enables an ideal environment for all these application software to work effectively. Hardware and software both are interdependent.























Let's personalize your content