A Hitchhiker?s Guide to Windows Containers
Linux Academy
MAY 15, 2020
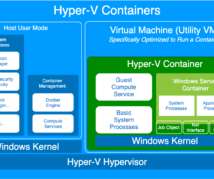
This article will give you the full lowdown on Windows Containers, to prepare you to do just that. Why Windows? First, I want to acknowledge that there is a big difference between Linux and Windows containers. So why do we even need Windows containers? Each running container is isolated inside a Hyper-V VM.

























Let's personalize your content