A Brief History of the Internet’s Biggest BGP Incidents
Kentik
JUNE 5, 2023
In this incident, a software bug caused a router to announce a large part of the IP address ranges present in the global routing table as if they were originated by AS7007. During the leak, a large portion of the internet’s traffic was redirected to AS7007, where it overwhelmed its networking equipment and was dropped.

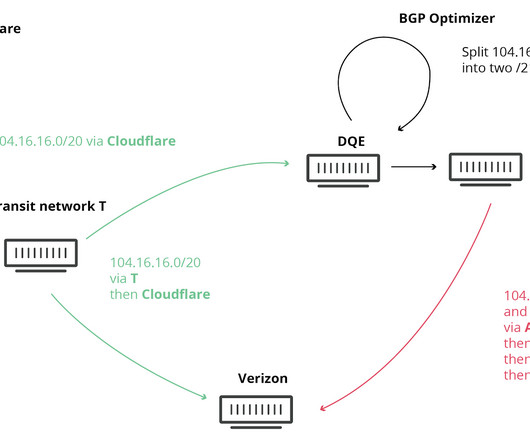


















Let's personalize your content