Cloudy with a chance of threats: Advice for mitigating the top cyber threats of 2024
Lacework
FEBRUARY 7, 2024
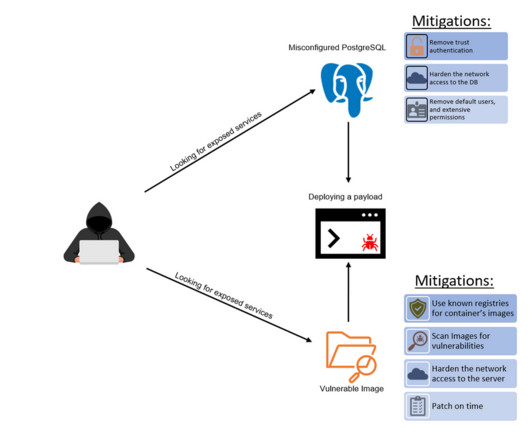
Developers are building systems and applications faster than ever, but this creates more risks and vulnerabilities for hackers to exploit. By integrating risk and threat insights, teams can prioritize the actions that matter most, like fixing critical vulnerabilities and stopping the most dangerous threat actors. Malware (e.g.,



































Let's personalize your content