Cybersecurity Snapshot: New Guide Details How To Use AI Securely, as CERT Honcho Tells CISOs To Sharpen AI Security Skills Pronto
Tenable
JANUARY 26, 2024
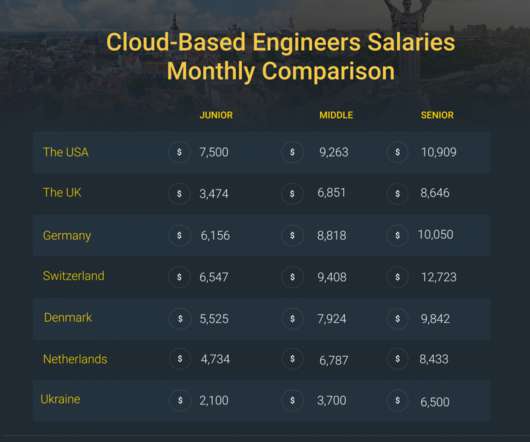
That’s the number one skill CISOs must acquire in 2024, according to Greg Touhill, Director of the CERT Division of Carnegie Mellon University’s Software Engineering Institute (SEI).






















Let's personalize your content