Deloitte Safeguards Software Development Lifecycle
Prisma Clud
AUGUST 10, 2023
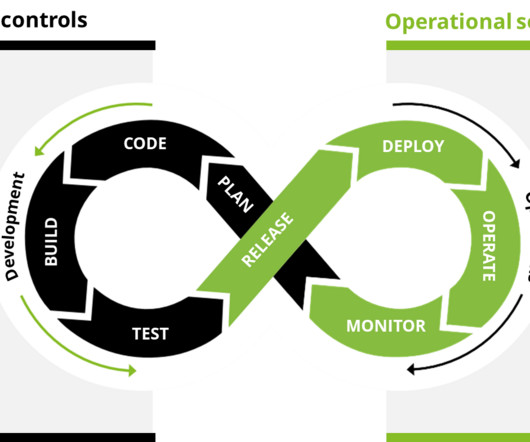
Palo Alto Networks and Deloitte have expanded their strategic alliance with a new SSDL offering to reinforce their customers' cloud environments with enhanced security measures from code to cloud. Adopting a shift left security approach empowers development teams to take ownership of security and promotes a proactive security mindset.






























Let's personalize your content