Kinsing Malware Hides Itself as a Manual Page and Targets Cloud Servers
Tenable
MAY 16, 2024
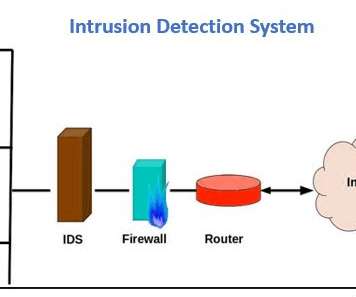
Background Cloud cryptomining has become an emerging trend in recent years, powered by the scalability and flexibility of cloud platforms. One of the most common cryptomining threats for cloud environments is the Kinsing malware. The Kinsing malware uses different locations to stay undetected and hides itself as a system file.















































Let's personalize your content