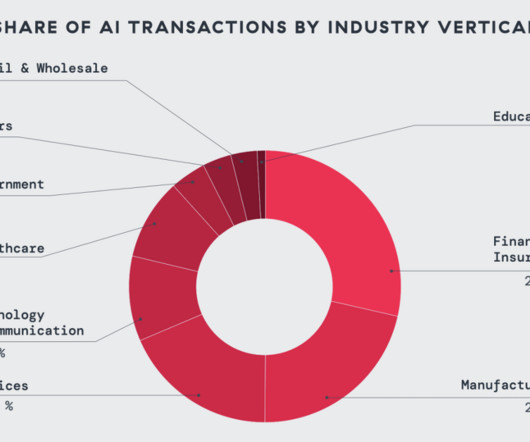
Chinese cyber espionage growing across all industry sectors
CIO
MARCH 4, 2025
Security researchers are warning of a significant global rise in Chinese cyber espionage activity against organizations in every industry. Researchers at the firm also identified seven new Chinese-origin cyber espionage groups in 2024, many of which exhibited specialized targeting and toolsets.


















































Let's personalize your content