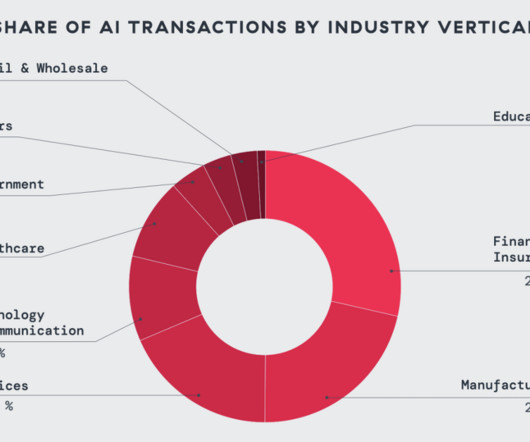
Chinese cyber espionage growing across all industry sectors
CIO
MARCH 4, 2025
Throughout 2024, China-nexus adversaries demonstrated increasingly bold targeting, stealthier tactics, and more specialized operations, CrowdStrike stated in its 2025 Global Threat Report. Vault Panda has used many malware families shared by Chinese threat actors, including KEYPLUG, Winnti, Melofee, HelloBot, and ShadowPad.
















































Let's personalize your content