Systems-level approach drives optimal performance and power efficiency for Linux and open-source workloads
CIO
JUNE 28, 2024
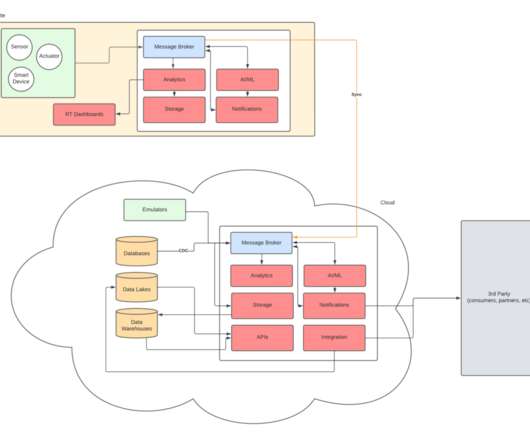
There is a greater need to optimize across the tech stack and take a systems-level approach. Microsoft is introducing a solution that balances performance and power efficiency for a range of Linux-based and open-source workloads.

















































Let's personalize your content