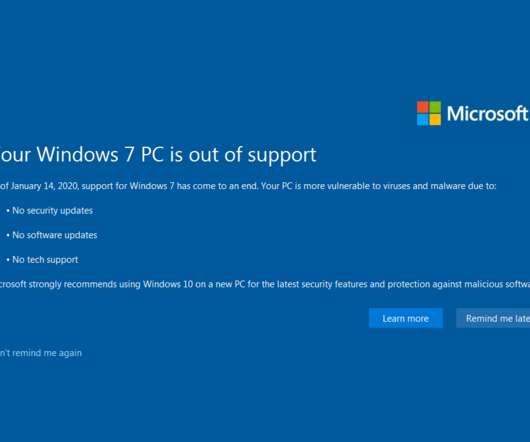
Stuck with Windows 7? Here’s a security game plan
The Parallax
JANUARY 21, 2020
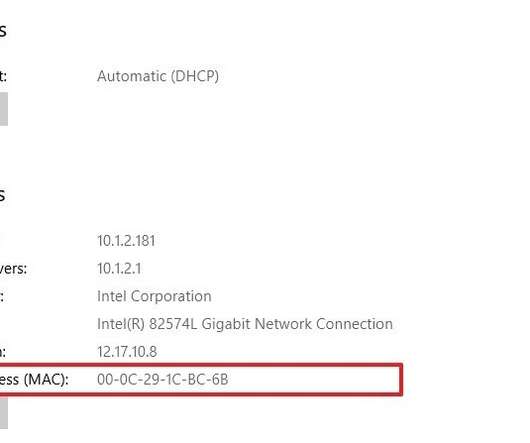
Last week, Microsoft’s Windows 7, once the go-to operating system of nearly 60 percent of all computers , reached the company’s designated end of the road for security patches. Like Windows XP before in 2014 , if you have a Windows 7 computer, it’s long past time for you to shell out some cash for a new one.













































Let's personalize your content