My New Year’s Resolution: Going Passwordless!
Ivanti
DECEMBER 29, 2021
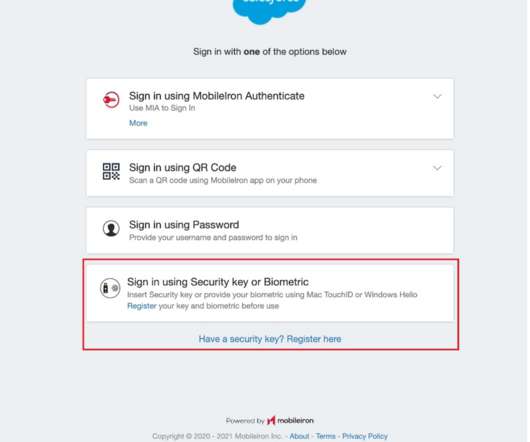
Another best practice that I started several years ago was to adopt a passwordless authentication initiative for all my internet connected personal devices. Contextual conditional access policies can be implemented to grant or deny access not only based on a trusted user, but also the trusted device, app, network (location), and time.
























Let's personalize your content