Ultraleap’s mid-air haptics tempts Tencent to join its $82M Series D fundraising
TechCrunch
NOVEMBER 17, 2021
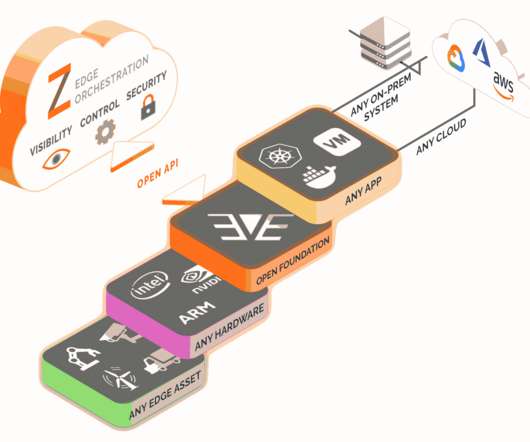
The underlying technology was based on post-graduate research from inventor – and still CEO – Tom Carter. Like the internet, it is a reality we will interact with, in all parts of life: at home, in the office, in cars, or out in public. The impressive ‘Star Wars’ demonstration took the crowd by storm.















































Let's personalize your content