Meter Command: the modern network interface
CIO
AUGUST 21, 2024
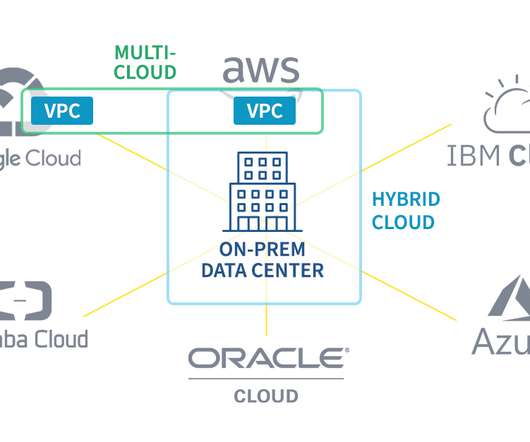
This rigidity is even more pronounced in infrastructure and networking. Infrastructure and networking, in particular, have been command-line interface (CLI) driven for decades. The last major change in networking software was moving from CLI to cloud management via dashboards, sacrificing precision for accessibility along the way.
















































Let's personalize your content