How to deploy software to Linux-based IoT devices at scale
InfoWorld
MARCH 20, 2024
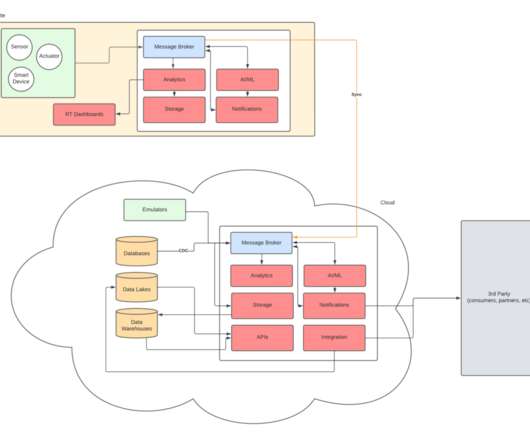
The internet of things (IoT) has transformed the way we interact with the world, connecting a myriad of devices to the internet, from smart thermostats in our homes to industrial sensors in manufacturing plants. In this article, we’ll explore some best practices for deploying software on large fleets of Linux-based IoT devices.


















































Let's personalize your content