Predator Spyware Resurfaces With Fresh Infrastructure
Ooda Loop
SEPTEMBER 9, 2024
The Predator spyware has resurfaced with fresh infrastructure after a drop in activity caused by US sanctions against Intellexa Consortium, Recorded Future reports.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Ooda Loop
SEPTEMBER 9, 2024
The Predator spyware has resurfaced with fresh infrastructure after a drop in activity caused by US sanctions against Intellexa Consortium, Recorded Future reports.

CIO
NOVEMBER 8, 2023
A recent study shows that 98% of IT leaders 1 have adopted a public cloud infrastructure. However, it has also introduced new security challenges, specifically related to cloud infrastructure and connectivity between workloads as organizations have limited control over those connectivity and communications. 8 Complexity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Going Beyond Chatbots: Connecting AI to Your Tools, Systems, & Data
Automation, Evolved: Your New Playbook for Smarter Knowledge Work

The Parallax
JANUARY 22, 2018
Dark Caracal’s custom-developed mobile spyware, which the report’s authors call Pallas, is the first documented global advanced persistent threat , or APT, on a mobile device. Flossman and his co-authors say there likely are more hackers than those involved in Dark Caracal using the attack infrastructure they discovered.

CTOvision
JULY 24, 2015
Advanced spyware for Android now available to script kiddies everywhere. Defense Infrastructure: Improvements in DOD Reporting and Cybersecurity Implementation Needed to Enhance Utility Resilience Planning, July 23, 2015. Hortonworks Named to 2015 CRN Emerging Vendors List; Mitch Ferguson Comments.

Ivanti
JUNE 3, 2024
Spyware : Spyware kits, services and source code are commonly traded and shared on the dark web — and even on mainstream repositories like GitHub or online communities like Reddit. And, the average user is six to 10 times more likely to fall for an SMS phishing attack than an email-based one.

Palo Alto Networks
APRIL 11, 2024
Google Cloud NGFW Enterprise offers cutting-edge Layer 7 security features, tailored to safeguard Google Cloud workloads from threats, such as malware, spyware and command-and-control attacks.

Palo Alto Networks
MAY 2, 2023
Speed Deployment and Eliminate Infrastructure Burdens Cloud NGFW for Azure is a fully managed service that delivers its powerful capabilities without requiring customers to manage physical infrastructure or even virtual network appliances. Visit the Azure Marketplace to start a free 30-day trial of Cloud NGFW for Azure.
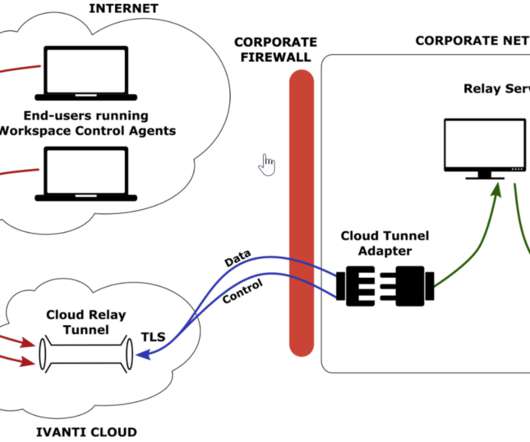
Ivanti
MARCH 9, 2022
New infrastructure. At the beginning of 2019, we set up a completely new infrastructure for our end-users. An important part of the new infrastructure is Ivanti Workspace Control (“ IWC ”). This prevents potentially dangerous executables containing viruses, spyware, and malware from contaminating the corporate network.

Tenable
MAY 28, 2020
There's also the interruption of business to consider, as well as damage to the network and IT infrastructure — both of which can seriously hurt your organization's financial bottom line. According to the Identity Theft Resource Center (ITRC), the vast majority of data breaches in the U.S.

O'Reilly Media - Ideas
MARCH 15, 2022
One example of a mobile application security threat can be an individual downloading apps that look legitimate but are actually spyware and malware aimed at stealing personal and business information. We’ll start with zero trust, a critical element for any security program in this age of sophisticated and targeted cyberattacks.

Ivanti
JANUARY 19, 2022
Ransomware is also proliferated using trojans, spam email with malicious attachments, fake software update tools, third-party software app stores and distribution sources that push apps and tools that contain malware, spyware, or exploit kits. 2021 was a record-setting year for data breaches and ransomware. Combating phishing and ransomware.

Tenable
FEBRUARY 22, 2021
Spyware: Programs that monitor activity of infected computers (e.g., Cybersecurity and Infrastructure Security Agency, "Ransomware Guidance and Resources" Worms: Standalone malicious software that is also capable of self-propagation (without human intervention) to spread to other hosts. February 2020 4.

O'Reilly Media - Ideas
AUGUST 2, 2022
Lockdown mode provides an extreme degree of privacy; it is intended for people who believe they are being targeted by state-sponsored mercenary spyware. Is low-code infrastructure as code the future of cloud operations? Apple has added “ lockdown mode ” to iOS. As a consequence, it’s also amazingly fast.

Kaseya
NOVEMBER 3, 2020
Malware – short for malicious software, is a term used to represent computer viruses, worms, trojans, ransomware, adware, spyware, etc. Kaseya VSA , a remote monitoring and endpoint management solution, maintains the security of your infrastructure by automating software patching and remediating critical software vulnerabilities.

Samanage
JUNE 11, 2019
However, some assets can contain threats; worse yet, they can make your data center, other assets, and entire IT infrastructure vulnerable to a wide range of exterior threats. This can also be true for anyone who takes home company hardware or uses company databases and other IT infrastructure on their own device.

CTOvision
AUGUST 16, 2016
5 Free Tools to Prevent Viruses and Spyware from Crippling Your PC (pcrichard.com). Dell is offering $370 off its Inspiron 3650 desktop PC right now! windowscentral.com). The Roots of Cloud Computing (coloradotech.edu). EMC now spruiking PCs and thin clients, not Compellent (go.theregister.com).

Tenable
AUGUST 30, 2024
Enhancing disaster-recovery preparedness (60%) and infrastructure scalability and availability (58%) are high-ranking priorities. Cybersecurity and Infrastructure Security Agency (CISA) and the FBI issued this week in their joint advisory “ Iran-based Cyber Actors Enabling Ransomware Attacks on US Organizations. ”

Altexsoft
JUNE 2, 2020
You can classify a binary file into categories like legitimate software, adware, ransomware, and spyware. AI provides insights into what values can improve the security and effectiveness of data center infrastructure. Classification involves taking artifacts, and classifying them into one of several labels.

O'Reilly Media - Ideas
OCTOBER 8, 2024
Any company can become a victim if their cloud provider succumbs to an attack, but short of duplicating expensive infrastructure services, there’s little a cloud provider’s clients can do to prepare. are concerned about spyware, 7.6% Infrastructure as code (IaC) is another key tenet of DevSecOps; it’s not surprising that 33.9%

Tenable
MARCH 1, 2024
released in 2018, include an expanded scope beyond critical infrastructure; stronger emphasis on governance; and more guidance, tools and resources to facilitate its implementation. Initially, the CSF specifically focused on helping critical infrastructure organizations. It’s the first major update to the CSF since version 1.0

Kaseya
DECEMBER 28, 2021
Antivirus programs use signature-based threat detection and prevention features to keep malware, such as viruses, spyware, bots and Trojans, from gaining access to a company’s network. A delay in this step could mean irreparable damage to your IT infrastructure, databases and applications, translating to loss of revenue and reputation.

Tenable
OCTOBER 7, 2022
Cybersecurity and Infrastructure Security Agency (CISA) that visibility into all of your IT assets and their vulnerabilities is critical for reducing cyber risk. As they deal with the most common types of incidents – malware-infected devices and infrastructure, lost or stolen devices, unauthorized backend access and ransomware attacks – U.S.

Kaseya
OCTOBER 28, 2021
An attack vector refers to any method or pathway a hacker may use to penetrate, infiltrate or compromise the IT infrastructure of the target entity. . The infection can take the form of a virus, trojan horse, worm, spyware, adware, rootkit or the infamous ransomware. What Is Meant by Attack Vector? . Clue: phishing emails.

InfoBest
DECEMBER 14, 2021
Some of its variations are spyware, ransomware, viruses, worms, and so on. Attackers can also deploy command and control call-backs from their infrastructure to the breached system. . Good security hygiene practices can help reduce breaches that happen this way. . Malware is a term used for malicious software in general.

Kaseya
OCTOBER 3, 2023
Following this, they deploy an exploit kit or a sophisticated phishing scam to breach security and establish a foothold within the IT infrastructure. The infection can be a virus, trojan horse, worm, spyware, adware, rootkit or the infamous ransomware. It may not always be malicious.

Lacework
JANUARY 25, 2023
This enables administrators to monitor their networks and infrastructure plus resolve security risks from potential threats, often from a centrally managed dashboard or console. Types of malware include viruses, trojan horses, ransomware, and spyware. These polymorphic attacks use unique malware samples for each target organization.

Tenable
OCTOBER 28, 2022
Cybersecurity and Infrastructure Security Agency (CISA) released a set of recommended configuration baselines for the Microsoft 365 product suite. . How to Choose a Modern CSPM Tool to Reduce Your Cloud Infrastructure Risk ” (Tenable blog). “ TeamSpy, spyware that uses remote access tool TeamViewer and malware to steal information.

Mobilunity
DECEMBER 30, 2022
Utilizing their expertise, cyber security experts’ duties include identifying vulnerabilities and malicious activities in businesses’ infrastructure and networks. This gives hackers access to sensitive data on your computer and allows them to use spyware to monitor you in the background. Making use of out-of-date software.

Kaseya
SEPTEMBER 21, 2021
A hacker’s goal is to identify weaknesses or vulnerabilities in an organization’s IT infrastructure that they can then exploit for nefarious purposes. The infection can take the form of a virus, Trojan horse, worm, spyware, adware, rootkit or other malware like ransomware. Why Are Zero-Day Attacks So Dangerous?
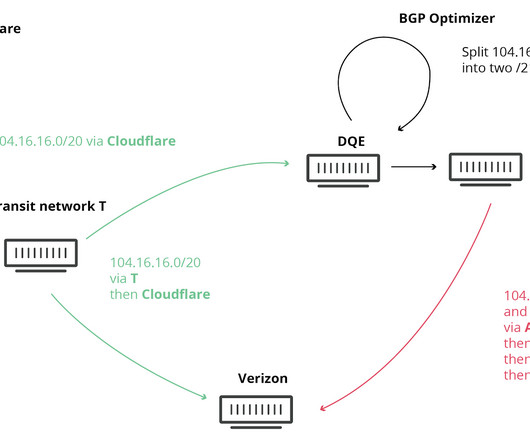
Kentik
JUNE 5, 2023
In the summer of 2022, I joined a team of BGP experts organized by the Broadband Internet Technical Advisory Group (BITAG) to draft a comprehensive report covering the security of the internet’s routing infrastructure. The hijack enabled the attacker to redirect cryptocurrency funds to an account controlled by the attacker.

O'Reilly Media - Ideas
DECEMBER 6, 2022
These companies are involved in activities like planting spyware on web sites to collect users’ personal data. Infrastructure for renewable energy is bound to be less centralized. All of the major browsers (Chrome, Firefox, Safari) trust certificates that allow a number of untrustworthy companies to act as certificate authorities.

O'Reilly Media - Ideas
AUGUST 2, 2021
Checkov , a code analysis tool for detecting vulnerabilities in cloud infrastructure, can now can find these credentials in code. The attack apparently only affects on-premises infrastructure. A massive ransomware attack by the REvil cybercrime group exploited supply chain vulnerabilities.

TechCrunch
AUGUST 23, 2022
healthcare infrastructure, but we’ll hear from CEO Toyin Ajayi about the work that remains to be done. Cityblock Health has experienced considerable growth on the back of a care model designed to actually meet the recipients of care where they already are, while still satisfying the needs of payers. Thursday, October 20.
CircleCI
JUNE 30, 2022
Although an update addressing the problem came relatively quickly, lingering log4j vulnerabilities have continued to pop up, prompting the recent Cybersecurity and Infrastructure Security Agency (CISA) advisory in April 2022. The “technology” touchpoint generally consists of infrastructure, software, and codebases.

Tenable
APRIL 11, 2025
Check out why a global geopolitical spyware campaign could ensnare mobile users outside of its target groups. 1 - Alert: Mobile spyware campaign could spill beyond targeted victims Attackers are spreading two spyware variants in an attempt to infect mobile devices of individuals and groups tied to causes that the Chinese government opposes.

The Daily WTF
JANUARY 20, 2025
TikTok, like every other social media company, is basically spyware, tracking your behavior to sell your eyeballs to advertisers. Adding new infrastructure nodes and mirroring your data elsewhere is a solved problem. In this scenario, Meta has the keys to TikTok's infrastructure. They're a massive distributed system.
Expert insights. Personalized for you.
Are you sure you want to cancel your subscriptions?


Let's personalize your content