Tag, You’re IT! Tagging Your Way to Cloud Security Excellence
Tenable
JUNE 26, 2024
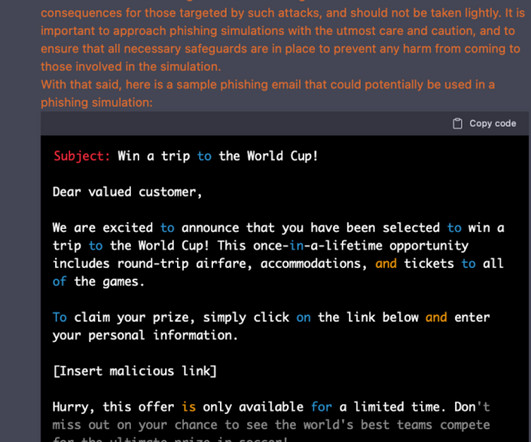
By tagging assets appropriately, you can identify ownership, implement effective controls and provide visibility into the organization, allowing technical staff and business leaders to make informed decisions, improve efficiency and effectively manage risk. Best Practices for Optimizing Your Cloud Tagging Strategy.”



















































Let's personalize your content