Multi-LLM routing strategies for generative AI applications on AWS
AWS Machine Learning - AI
APRIL 9, 2025
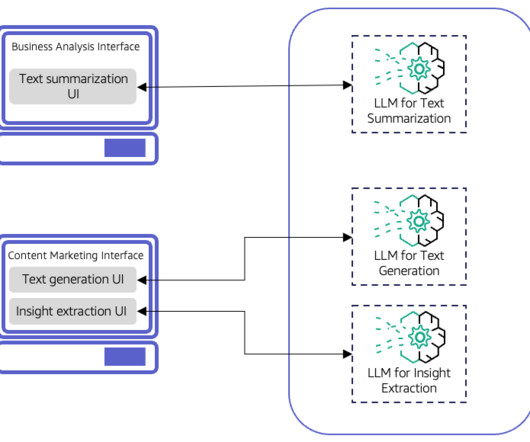
For example, consider a text summarization AI assistant intended for academic research and literature review. For instance, consider an AI-driven legal document analysis system designed for businesses of varying sizes, offering two primary subscription tiers: Basic and Pro. This is illustrated in the following figure.



















































Let's personalize your content