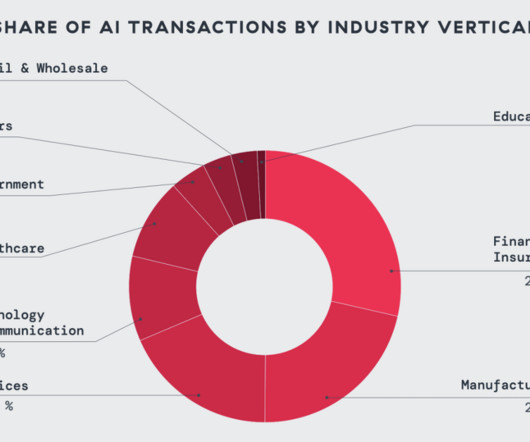
Chinese cyber espionage growing across all industry sectors
CIO
MARCH 4, 2025
The report also highlighted that Chinese groups continue to share malware tools a long-standing hallmark of Chinese cyber espionage with the KEYPLUG backdoor serving as a prime example. Vault Panda has used many malware families shared by Chinese threat actors, including KEYPLUG, Winnti, Melofee, HelloBot, and ShadowPad.















































Let's personalize your content