9 IT skills where expertise pays the most
CIO
APRIL 25, 2025
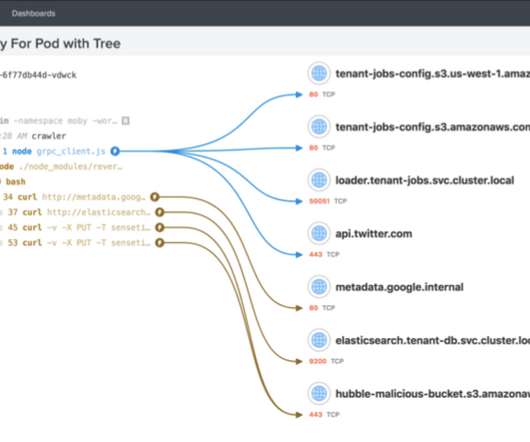
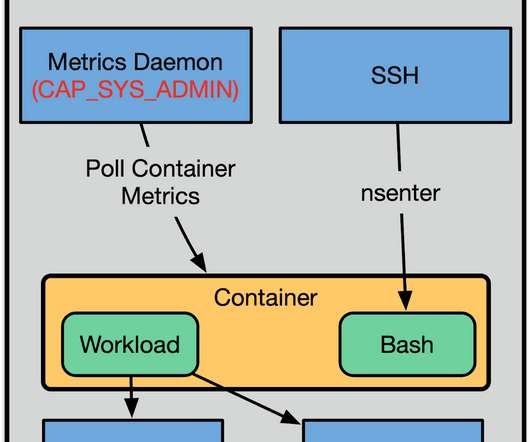
However, expertise in these particular nine skills is likely to earn you a pay bump across any industry, as technology has become vital for typical business operations. Bash Average salary: $126,473 Expertise premium: $11,032 (8%) BASH is a scripting command-line interface shell program used for scripting in Linux and MacOS.












































Let's personalize your content