With $29M in funding, Isovalent launches its cloud-native networking and security platform
TechCrunch
NOVEMBER 10, 2020
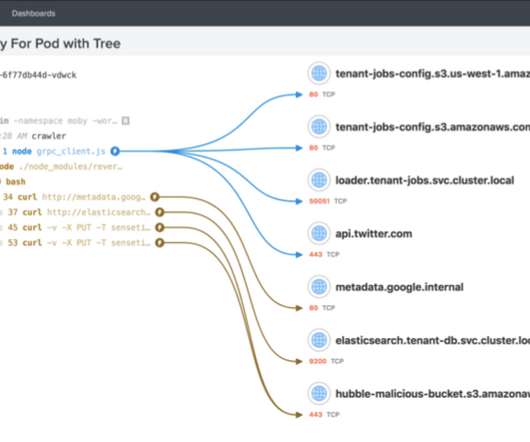
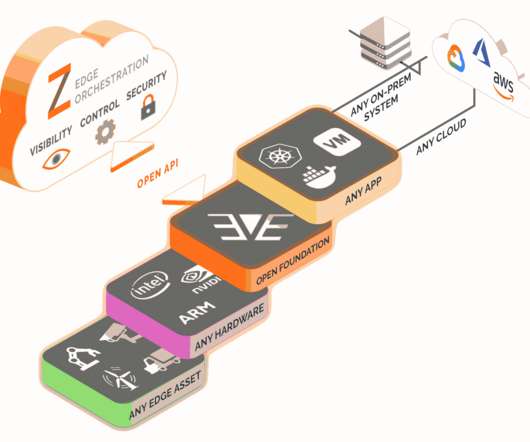
Isovalent , a startup that aims to bring networking into the cloud-native era, today announced that it has raised a $29 million Series A round led by Andreesen Horowitz and Google. The founding team of CEO Dan Wendlandt and CTO Thomas Graf has deep experience in working on the Linux kernel and building networking products.








































Let's personalize your content