Cybersecurity Snapshot: New Guides Offer Best Practices for Preventing Shadow AI and for Deploying Secure Software Updates
Tenable
OCTOBER 25, 2024
s cyber agency has found.

Tenable
OCTOBER 25, 2024
s cyber agency has found.

elsua: The Knowledge Management Blog
JUNE 4, 2008
Toolbox for IT Join Now / Sign In My Home Posts Connections Groups Blogs People Communities Vendors Messages Profile Achievements Journal Blog Bookmarks Account / E-mails Topics Business Intelligence C Languages CRM Database IT Management and Strategy Data Center Data Warehouse Emerging Technology and Trends Enterprise Architecture and EAI ERP Hardware (..)
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tenable
MARCH 14, 2025
Crypto agility describes the capabilities needed to replace and adapt cryptographic algorithms for protocols, applications, software, hardware, and infrastructures without interrupting the flow of a running system to achieve resiliency, reads a NIST statement about the new publication. CIS SUSE Linux Enterprise 15 Benchmark v2.0.1

elsua: The Knowledge Management Blog
JUNE 4, 2008
Toolbox for IT Join Now / Sign In My Home Posts Connections Groups Blogs People Communities Vendors Messages Profile Achievements Journal Blog Bookmarks Account / E-mails Topics Business Intelligence C Languages CRM Database IT Management and Strategy Data Center Data Warehouse Emerging Technology and Trends Enterprise Architecture and EAI ERP Hardware (..)

Tenable
NOVEMBER 15, 2024
Maintain a continuously updated inventory of all your assets – both hardware and software, and on-prem and in the cloud. These are just a few of the questions in the AI security systems section: How are security vulnerabilities actively identified and mitigated in software and hardware components? and the U.S. CIS Apple macOS 13.0
Altexsoft
FEBRUARY 11, 2020
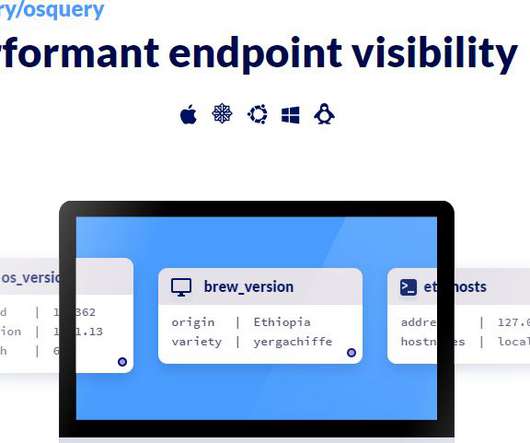
The team follows a set of guidelines and processes laid out in your incident response plan. You can use Wazuh in a Docker container or on Linux, Windows, and macOS systems. You can use GRR in a Docker container or on standard Linux systems. You can use Osquery on Windows, Linux, and macOS machines.

Altexsoft
MAY 20, 2020
Namely, these layers are: perception layer (hardware components such as sensors, actuators, and devices; transport layer (networks and gateway); processing layer (middleware or IoT platforms); application layer (software solutions for end users). Perception layer: IoT hardware. How an IoT system works.
Let's personalize your content