Need a security road map? Ditch the ad hoc measurement
CIO
SEPTEMBER 17, 2024
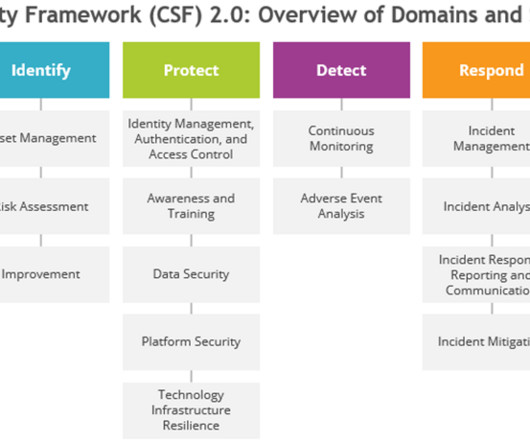
CISOs can only know the performance and maturity of their security program by actively measuring it themselves; after all, to measure is to know. However, CISOs aren’t typically measuring their security program proactively or methodically to understand their current security program.















































Let's personalize your content