Yes, you have to update your Apple devices again, because spyware is bad
TechCrunch
SEPTEMBER 22, 2023
Apple has released urgent security updates for iPhones, iPads, Macs, Apple Watch, and Safari users to block two active spyware campaigns.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

TechCrunch
SEPTEMBER 22, 2023
Apple has released urgent security updates for iPhones, iPads, Macs, Apple Watch, and Safari users to block two active spyware campaigns.

TechCrunch
SEPTEMBER 27, 2021
Mobile spyware is one of the most invasive and targeted kinds of unregulated surveillance, since it can be used to track where you go, who you see and what you talk about. And because of its stealthy nature, mobile spyware can be nearly impossible to detect. “We already know applications that are spyware.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

TechCrunch
JULY 15, 2022
Journalists and activists are increasingly targeted by the wealthy and resourceful who seek to keep the truth hidden, from nation-state aligned hackers hacking into journalist’s inboxes to governments deploying mobile spyware to snoop on their most vocal critics. Runa Sandvik, founder of Granitt. Image: (supplied).

TechCrunch
APRIL 11, 2023
” Small towns and local governments are largely unable to fend off ransomware attacks on their own. Nation-state hackers are undermining human rights and the security and privacy of millions by hacking into phones using undisclosed security flaws. How do we know to trust the security of the phones in our pockets?

TechCrunch
OCTOBER 4, 2023
Microsoft has released patches to fix zero-day vulnerabilities in two popular open source libraries that affect several Microsoft products, including Skype, Teams and its Edge browser. But Microsoft won’t say if those zero-days were exploited to target its products, or if the company knows either way.

The Parallax
MAY 7, 2018
Researchers announced on May 1 that when they inspected the ingredients of the North Korean antivirus software for Windows computers, they found a mix of spyware and old code stolen from an antivirus vendor. READ MORE ON SECURITY AND GEOPOLITICS. How antivirus software could be used for government espionage.

TechCrunch
DECEMBER 1, 2023
Apple has released security updates for iPhones, iPads and Macs to patch against two vulnerabilities, which the company says are being actively exploited to hack people. following a vulnerability disclosure by security researchers at Google’s Threat Analysis Group, which investigates […] © 2023 TechCrunch. and macOS 14.1.2,

Ivanti
JUNE 3, 2024
Not surprisingly, this has created an escalating vulnerability gap: more mobile devices means more mobile threats — and more blind spots as IT and security teams scramble to identify all those devices as they connect to their networks.

O'Reilly Media - Ideas
MARCH 15, 2022
The future of cybersecurity is being shaped by the need for companies to secure their networks, data, devices, and identities. This includes adopting security frameworks like zero trust, which will help companies secure internal information systems and data in the cloud. Zero Trust Security.

O'Reilly Media - Ideas
OCTOBER 8, 2024
In August 2024, we asked our customers to tell us about security: their role in security, their certifications, their concerns, and what their companies are doing to address those concerns. We had 1,322 complete responses, of which 419 (32%—roughly one-third) are members of a security team. are managers, 7.2% That gives us 27.9%

CTOvision
JULY 6, 2015
Google-style recruiting — even in government FCW (Today) - Hire people who are better than you, and make sure they’re smart and curious, says Google exec Laszlo Bock.Google is famous for its culture of work as play. Dezzutti has been instrumental in Market Connections’ efforts to provide views and trends to government.

Tenable
AUGUST 30, 2024
And get the latest on AI-system inventories, the APT29 nation-state attacker and digital identity security! For more information about cybersecurity threats to educational institutions: “ Cybersecurity Preparedness for K-12 Schools and Institutions of Higher Education ” (U.S.

Altexsoft
FEBRUARY 6, 2021
The rapidly growing volume and sophistication of attacks entail the need for greater preparedness, especially through regular security exercises. Here’s a question related to the field of security: Why do military organizations ceaselessly conduct combat exercises or drills? Security validation is necessary for many compelling reasons.

TechBeacon
SEPTEMBER 16, 2022
Once the message is opened (or, possibly, even if it's not), the victimized endpoint is at the mercy of the spyware’s commands. The story is as old as phishing itself. A malicious message is sent, disguised as something innocuous.

Tenable
FEBRUARY 22, 2021
When you're new to vulnerability assessment (VA) – or any other area of cybersecurity, for that matter – some aspects of the process might seem unfamiliar or confusing. This is particularly true of the jargon; cybersecurity and technology as a whole have a long list of specialized terminology. . Here’s a brief introduction.

Tenable
MAY 28, 2020
Learn more about the key threat vectors you will need to combat with vulnerability assessment tools and cybersecurity best practices. The modern cybersecurity landscape is incredibly complex by any standard. You must leverage strong cybersecurity measures, including penetration testing and threat modeling.
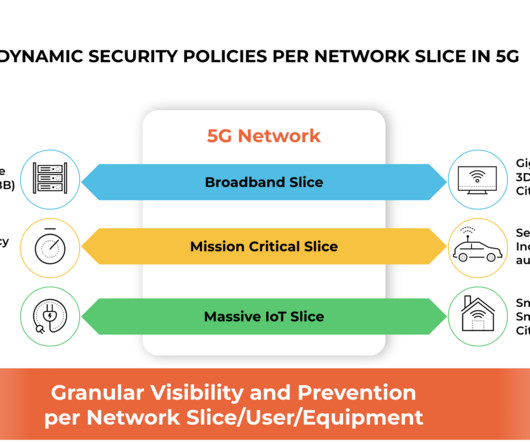
Palo Alto Networks
FEBRUARY 27, 2023
Our work with Singtel focuses on application-layer security, 5G network slice security, intelligent security per 5G subscriber and equipment identities. The role of cybersecurity has become increasingly important. Application-Layer Security Application-layer security has a few dimensions.

Tenable
MAY 7, 2020
Ransomware attacks are particularly and increasingly prevalent, especially against health care facilities and state or local government agencies. These facts all point to the big-picture existential threat posed by cyberattacks and network security threats. 3 And the types of ransomware deployed are more complex than ever.

Palo Alto Networks
JANUARY 23, 2023
It should come as no surprise that cybersecurity is, once again, priority #1 for state CIOs. Perhaps it’s because none of the other initiatives on the list (not even hybrid work, legacy modernization or cloud adoption) can succeed without a solid cybersecurity foundation. And, they’re innovating faster than ever before.

O'Reilly Media - Ideas
AUGUST 2, 2021
Security continues to be in the news: most notably the Kaseya ransomware attack, which was the first case of a supply chain ransomware attack that we’re aware of. However, the biggest problem in security remains simple: take care of the basics. That’s new and very dangerous territory.

Mobilunity
DECEMBER 30, 2022
If you have an IT team, keep in mind that they don’t always have time to conduct a comprehensive cybersecurity assessment because they are already overwhelmed with day-to-day tasks. Therefore, many businesses hire cybersecurity experts to join their teams and take care of security tasks. Making use of out-of-date software.

Tenable
OCTOBER 28, 2022
Get the latest on Microsoft 365 security configurations; effective CISO board presentations; rating MSPs’ cybersecurity preparedness; and hospitals’ Daixin cyberthreat. Cybersecurity and Infrastructure Security Agency (CISA) released a set of recommended configuration baselines for the Microsoft 365 product suite. .

CTOvision
DECEMBER 4, 2014
Regin, new computer spyware, discovered by Symantec. A leading computer security company says it has discovered one of the most sophisticated pieces of malicious software ever seen. Symantec says the bug, named Regin, was probably created by a government and has been used for six years against a range … Read more on BBC News.

Samanage
JANUARY 29, 2019
Improving IT Security through a Sound IT Strategy. In fact, by the midpoint of 2018, the IT Governance Blog reported that there had already been more than 600 data breaches that year. What’s more important is world governments are beginning to hold companies and other institutions accountable for their cybersecurity and data breaches.

O'Reilly Media - Ideas
DECEMBER 6, 2022
AI governance –including the ability to explain and audit results–is a necessity if AI is going to thrive in an era of declining public trust and increasing regulation. There are obvious ramifications for privacy and security, though users can start and stop recording. 95% of all web applications have security holes.

Kaseya
DECEMBER 28, 2021
Endpoint protection, also known as endpoint security, involves the use of advanced security tools and processes to secure various endpoints like servers, workstations and mobile devices that connect to a corporate network. The global endpoint security market is projected to continue to grow to over $19 billion in 2025.

Hu's Place - HitachiVantara
MAY 10, 2019
These new technologies open up new risks such as phishing, identity theft, card skimming, viruses and Trojans, spyware and adware, social engineering, website cloning and cyber stalking and vishing (If you have a mobile phone, you’ve likely had to contend with the increasing number and sophistication of vishing scams).

Kaseya
OCTOBER 3, 2023
Endpoint detection and response (EDR) is among the latest breed of security software designed to keep emerging and sophisticated cyberthreats like ransomware at bay. Our blog provides all the information you need about EDR. Endpoint security is the first line of defense for any organization. Give it a read. What is EDR?

Kaseya
SEPTEMBER 21, 2021
Once bad actors gain access to an organization’s computer network, they can damage the business by blocking access, encrypting systems and data to demand a ransom, or surreptitiously stealing crucial information that can fetch them a tidy sum on the dark web. Software vulnerabilities pose serious cybersecurity risks.

TechCrunch
JANUARY 11, 2022
Today we have new venture funds, spyware news, Brex raising (again), and more. Cybersecurity matters to democracy : Spyware built by the infamous NSO Group was “used to spy on three critics of the Polish government,” according to Citizen Lab, TechCrunch reports. Hello and welcome to Daily Crunch for January 11, 2022!

Tenable
MARCH 1, 2024
Check out what’s new in NIST’s makeover of its Cybersecurity Framework. Also, how to assess the cybersecurity capabilities of a generative AI LLM. 1 - NIST’s Cybersecurity Framework 2.0 1 - NIST’s Cybersecurity Framework 2.0 The Cybersecurity Framework at 10.and And the most prevalent malware in Q4. And much more!

The Parallax
JANUARY 22, 2018
The digital-rights group Electronic Frontier Foundation and Lookout Mobile Security, which co-authored the report, say they tracked the Dark Caracal phishing campaign across more than 60 websites. ”—Michael Flossman, senior security researcher, Lookout Mobile Security.

TechCrunch
JULY 6, 2022
In cybersecurity news, hotel giant Marriott found itself on the wrong side of another data breach , Carly writes. government that North Korean hackers are targeting some of the country’s healthcare organizations with their ransomware. She also laid out a claim by the U.S. She also laid out a claim by the U.S. Do you want a ride?

Tenable
OCTOBER 7, 2022
7 | CISA puts spotlight on asset inventory and vulnerability management | Think tank does deep dive on IoT security | What’s the current state of cybersecurity? As Cybersecurity Awareness Month kicks off, here’s a fresh reminder from the U.S. Cloud Security: Why You Shouldn’t Ignore Ephemeral Assets.
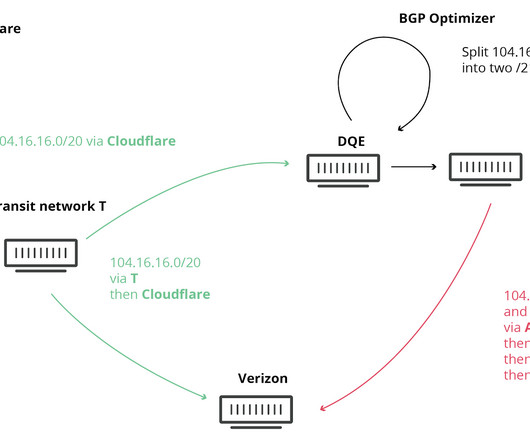
Kentik
JUNE 5, 2023
In the summer of 2022, I joined a team of BGP experts organized by the Broadband Internet Technical Advisory Group (BITAG) to draft a comprehensive report covering the security of the internet’s routing infrastructure. Routing security incidents in the wild BGP routing incidents can be problematic for a range of reasons.
TechCrunch
AUGUST 11, 2023
If you turn up at the doors, just a pair of levitating buttocks, we have achieved some sort of superconduction, but you’ll have made an ass of yourself, and security will probably turn you away) to TechCrunch Disrupt, where we have a whole Sustainability Stage planned ! Oh, governments. They do try ever so hard. this week.
CircleCI
JUNE 30, 2022
For developers, several high-profile software security exploits have recently underscored the risks inherent in a similar type of supplier network: the software supply chain. It also includes building orchestrators and tools such as assemblers, compilers, code analyzers and repositories, security, monitoring, and logging ops tools.

The Daily WTF
JANUARY 20, 2025
TikTok, like every other social media company, is basically spyware, tracking your behavior to sell your eyeballs to advertisers. So, instead, we play Whac-a-Mole with apps, dressing up Sinophobia as a national security threat, and we dance around the 1st Amendment issues. All in all, it looks bleak.
Expert insights. Personalized for you.
Are you sure you want to cancel your subscriptions?


Let's personalize your content