SASE success: Avoid confusion and embrace a single-vendor solution
CIO
NOVEMBER 2, 2023
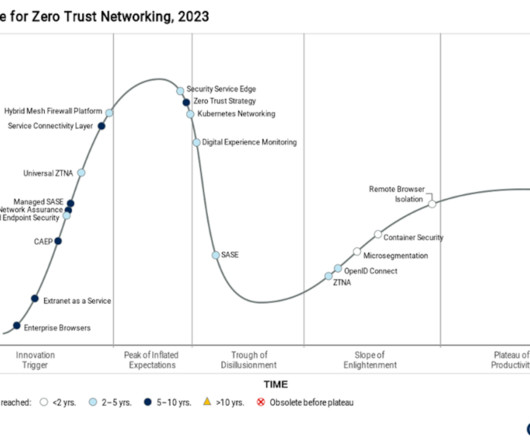
In the recent Gartner® Hype Cycle TM for Zero Trust Networking, 2023 report , which evaluates the current status of 19 of “the most relevant and hyped” zero-trust technologies, the cybersecurity industry analysts made a somewhat startling pronouncement about secure access service edge (SASE). 3 Why the trough of disillusionment?

























Let's personalize your content