AI in the Enterprise: 5 key findings of AI usage and threat trends
CIO
MARCH 25, 2025
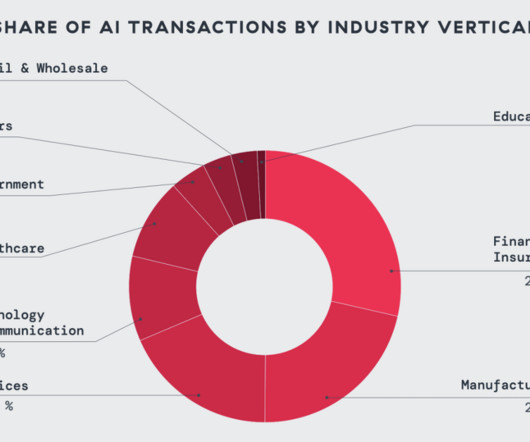
AI/ML usage surged exponentially: AI/ML transactions in the Zscaler cloud increased 36x (+3,464.6%) year-over-year, highlighting the explosive growth of enterprise AI adoption. Zscaler Figure 1: Top AI applications by transaction volume 2. Enterprises blocked a large proportion of AI transactions: 59.9%
























Let's personalize your content