How to Use a Firewall for Network Traffic Analysis and Behavioral Detection
Palo Alto Networks
FEBRUARY 21, 2020
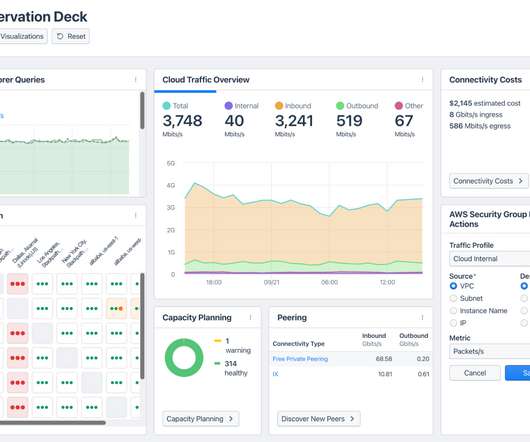
On March 17, we’ll host a webinar called “ Leverage Your Firewall to Expose Attackers Hiding in Your Network ” to share tips on how you can use your firewall for network traffic analysis. Network traffic analysis (NTA) – sometimes called network detection and response – is one such tool that provides that visibility.



















































Let's personalize your content