Optimizing Retailer Revenue with Sales Forecasting AI
Toptal
JULY 2, 2020
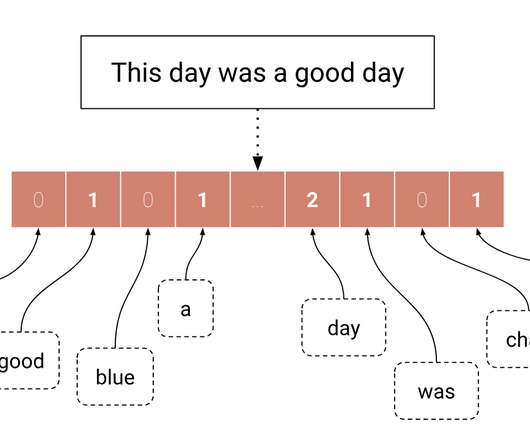
Retailers often face supply and demand issues that cause them to miss out on potential sales or tie up a lot of money in overstocked products. In this article, Toptal Data Scientist Ahmed Khaled explains how retailers can boost revenues and cut costs with sales forecasts backed by artificial intelligence.






































Let's personalize your content