What is Filegroup in Sql Server? When & How to Create?
The Crazy Programmer
JUNE 11, 2022
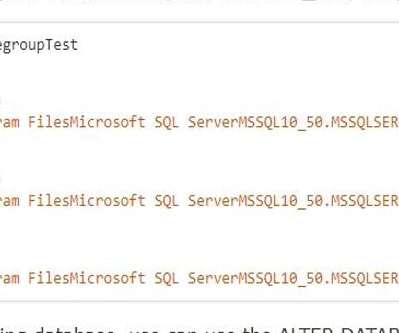
SQL Server database is a term you’re probably already familiar with. When it comes to storing large amounts of data, databases are extremely useful. And as you’ve figured out, SQL Server’s default settings aren’t always the best. When working with new user databases, this is the case. We can define a database as, In SQL Server, a database would be composed of a set of tables that store a particular set of structured data.







































Let's personalize your content