How to Hire Tech-Savvy Teachers for Blended Learning
PowerSchool
MAY 27, 2020
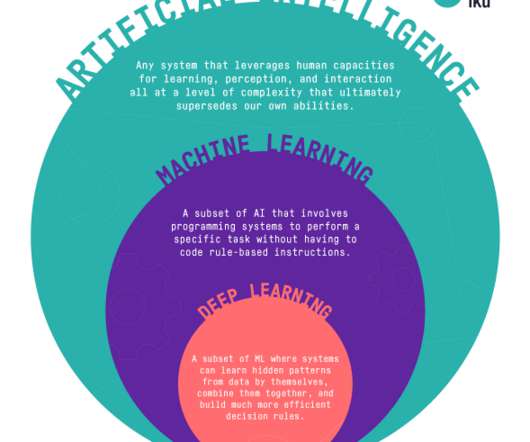
Online recruiting and hiring became an overnight necessity as a result of COVID-19 school closures, but this only accelerated a growing trend. It’s long been clear that paperless recruiting, hiring, and onboarding saves time and money; however, we’re now seeing how it helps schools and districts find and hire the tech-savvy educators they need to thrive in a future of blended and distance learning.


































Let's personalize your content