Exponential Backoff Retry Strategy in Test Automation
Perficient
AUGUST 27, 2024
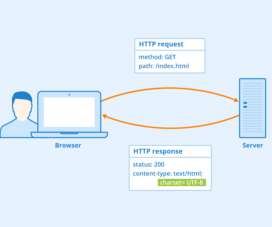
Introduction A highly effective strategy for managing flaky tests and unpredictable responses is the exponential backoff retry mechanism. This blog explores the concept of exponential backoff, its implementation in Katalon Studio, and practical scenarios where this strategy can be particularly beneficial.



















































Let's personalize your content