Can you have too many security tools?
CIO
AUGUST 29, 2024
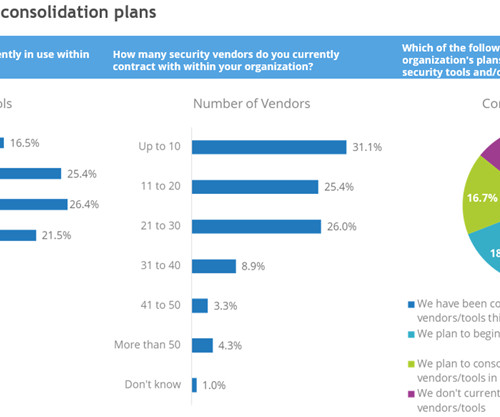
Tools that can help with security tool discovery include: Software asset management (SAM) tools, which identify software in the environment. Schwartz is an adjunct research advisor with IDC’s IT Executive Programs (IEP), focusing on IT business, digital business, disaster recovery, and data management.

















































Let's personalize your content