10 top priorities for CIOs in 2025
CIO
JANUARY 13, 2025
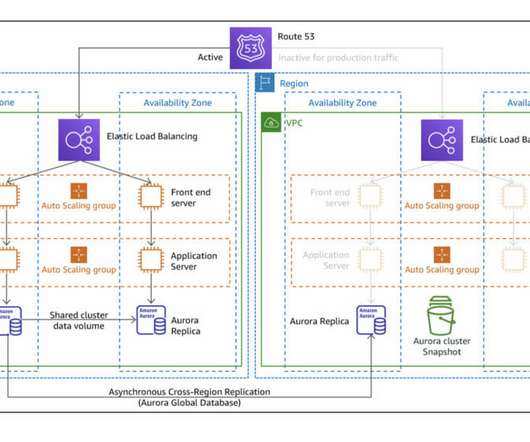
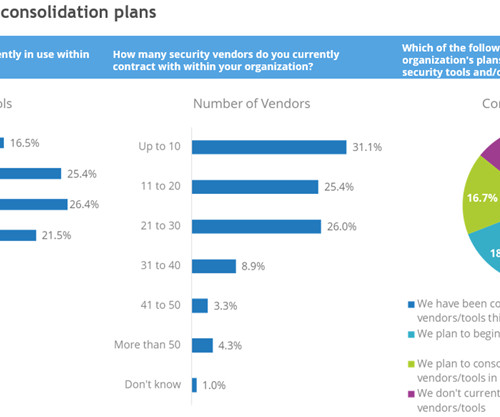
Double down on cybersecurity In 2025, there will be an even greater need for CIOs to fully understand the current cybersecurity threat landscape. Drafting and implementing a clear threat assessment and disaster recovery plan will be critical.









































Let's personalize your content