How Cloud Security Influences IoT Security
Xebia
OCTOBER 27, 2022
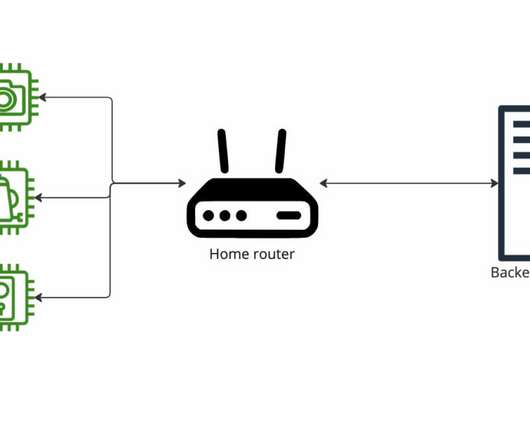
I keep on finding security issues at IoT vendors cloud services, and that saddens me. That is why I joined Xebia to learn more about cloud security and help IoT vendors to fix security issues with their cloud infrastructure. The default security of our IoT devices are improving. A typical IoT device network.


















































Let's personalize your content