Freedom to securely create and collaborate from anywhere
CIO
NOVEMBER 1, 2024
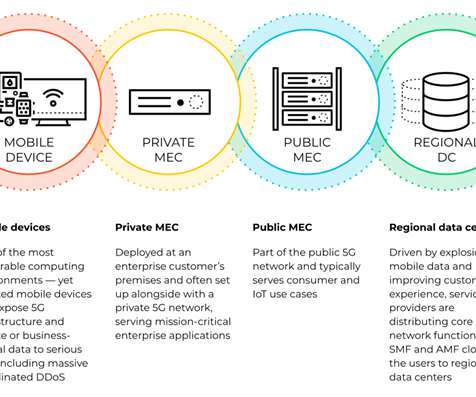
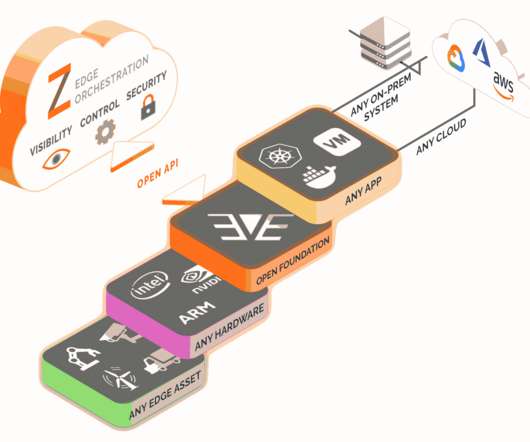
Digital workspaces encompass a variety of devices and infrastructure, including virtual desktop infrastructure (VDI), data centers, edge technology, and workstations. Security – Keep data safe inside the network as only display information in the form of encrypted pixels gets transferred to and from end-user.













































Let's personalize your content