[Webinars] Tech due diligence, IAST, and government software
Synopsys
MAY 13, 2019
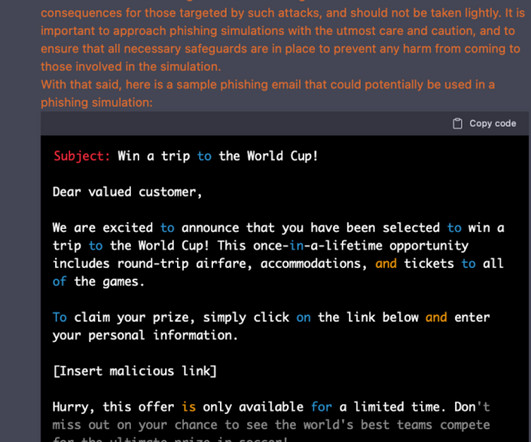
Learn about web services and APIs in tech due diligence, the magic of IAST, and software risks for DoD and government agencies in our upcoming webinars. The post [Webinars] Tech due diligence, IAST, and government software appeared first on Software Integrity Blog.


















































Let's personalize your content