Can serverless fix fintech’s scaling problem?
CIO
FEBRUARY 11, 2025
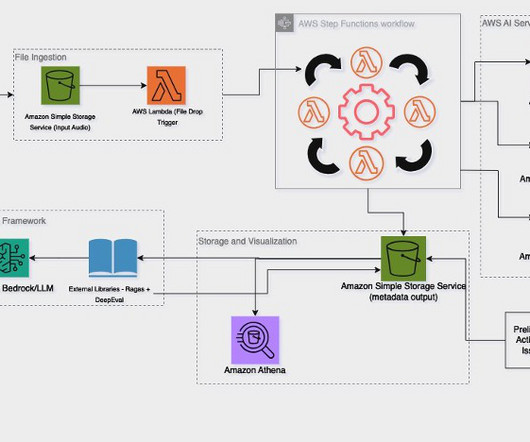
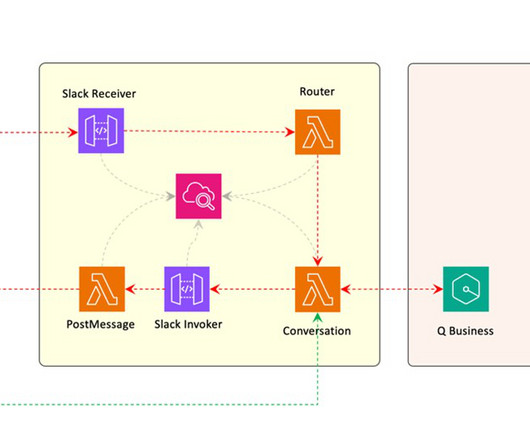
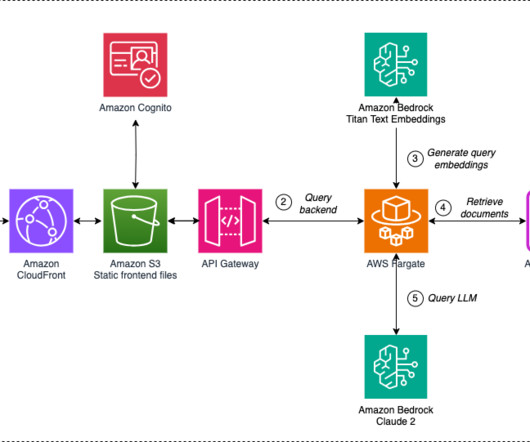
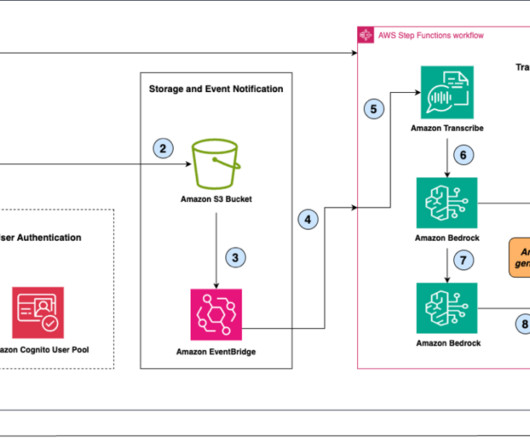
Add to this the escalating costs of maintaining legacy systems, which often act as bottlenecks for scalability. The latter option had emerged as a compelling solution, offering the promise of enhanced agility, reduced operational costs, and seamless scalability. For instance: Regulatory compliance, security and data privacy.













































Let's personalize your content