Scores of Organizations Hit By Novel Voldemort Malware
Ooda Loop
SEPTEMBER 3, 2024
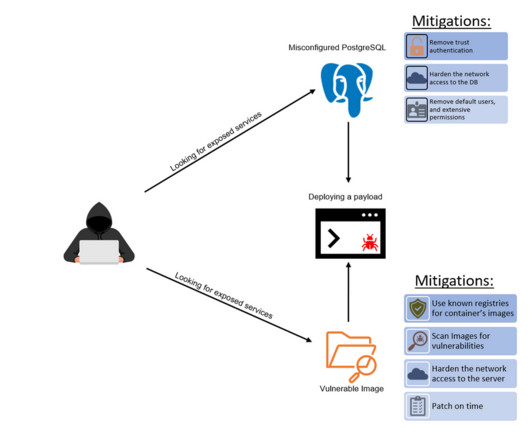
Researchers have uncovered a widespread malware campaign against entities in several countries. Researchers have uncovered a new malware campaign that makes use of several complex techniques to infiltrate victim’s systems.















































Let's personalize your content