What is Gateway in Computer Network – Types, Examples, Functions
The Crazy Programmer
SEPTEMBER 25, 2021
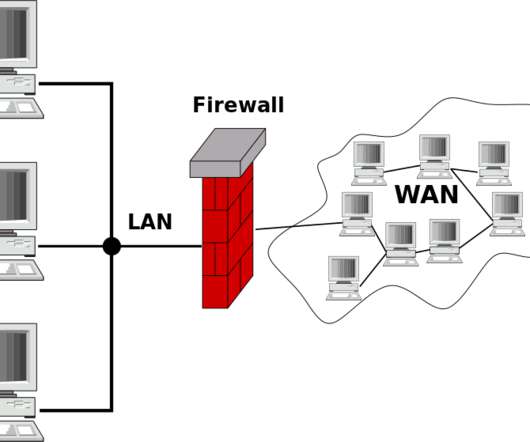
A gateway in the computer network is the node of the network used in telecommunication to connect the two different networks. Here both networks hold different transmission protocols hence we need to use the network node for networking. Gateways are capable of being used for LAN and WAN network connections.
































Let's personalize your content