11:11 Systems: Empowering enterprises to modernize, protect, and manage their IT assets and data
CIO
NOVEMBER 1, 2024
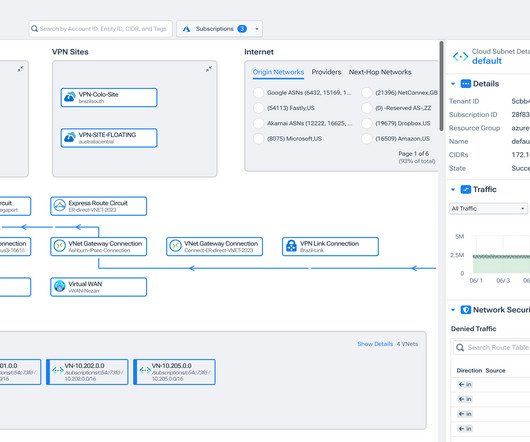
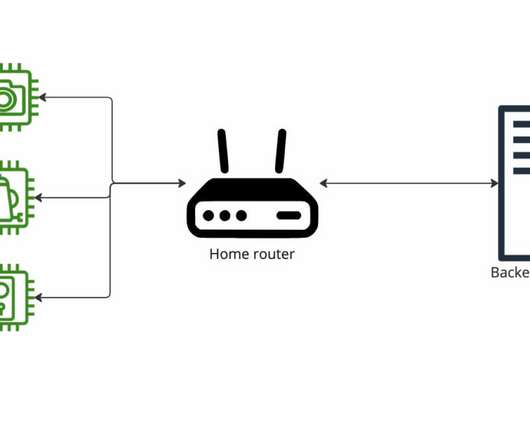
Virtually every company relied on cloud, connectivity, and security solutions, but no technology organization provided all three. Leaders across every industry depend on its resilient cloud platform operated by a team of industry veterans and experts with extensive networking, connectivity, and security expertise.
















































Let's personalize your content