Document Security is More than Just Password-Protection
CIO
OCTOBER 4, 2023
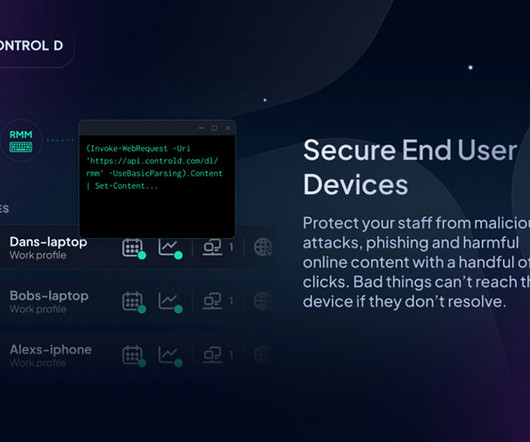
Today, PDF is considered the de facto industry standard for documents that contain critical and sensitive business information. In fact, it is estimated that more than three (3) trillion PDFs – from confidential business strategies and insights to sales agreements to legal contracts – are shared every day worldwide.




















































Let's personalize your content