The Importance of Security and Compliance in Enterprise Applications
OTS Solutions
JUNE 21, 2023
However, as more organizations rely on these applications, the need for enterprise application security and compliance measures is becoming increasingly important. Breaches in security or compliance can result in legal liabilities, reputation damage, and financial losses.













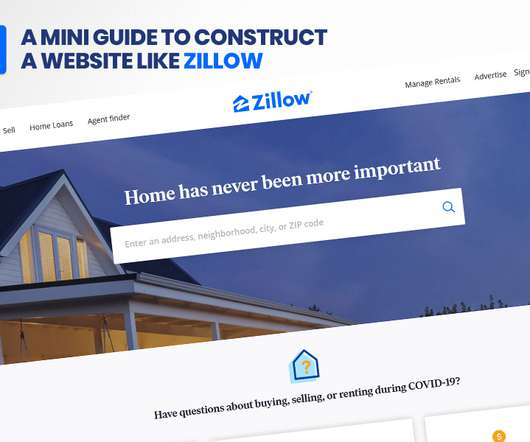













Let's personalize your content