Fixed wireless access (FWA) is a secure networking option
CIO
DECEMBER 19, 2023
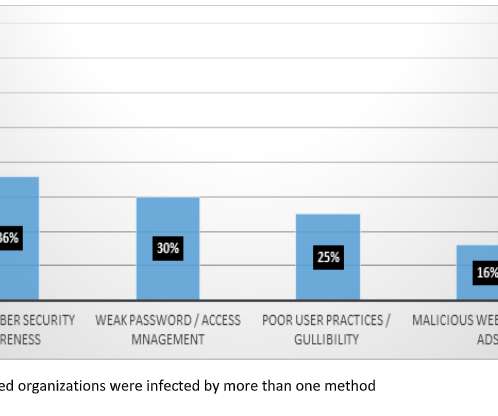
Modern security challenges Data from the Verizon 2023 Data Breach Investigations Report (DBIR) shows the three primary ways in which attackers access an organization are stolen credentials, phishing and exploitation of vulnerabilities. Customers can review reports on threats blocked via a special portal.









































Let's personalize your content